Symmetric and Asymmetric Encryption
What is Encryption and Cryptographic Keys?
Encryption is actually an age-old practice dating back to the times of the famous Roman king Caesar, who encrypted his messages using a Caesar cipher. The practice can be viewed as a transformation of information whereby the sender uses plain text, which is then encoded into cipher text to ensure that no eavesdropper interferes with the original plain text. On receiving the encoded message, the intended receiver decrypts it to obtain the original plain text message.
Once the transaction data encrypted then it can only be decrypted using the appropriate keys, its called a “Cryptographic keys“. A cryptographic key is a password which is used to encrypt and decrypt information.
There are two types of cryptographic keys. They are known as symmetric key and asymmetric key cryptography: symmetric and asymmetric encryption.
What is Symmetric Encryption?
Symmetric Encryption also called Secret Key Cryptography, it employs the same secret key for both encryption and decryption, that is used to exchange information during a secure session between the client’s browser and web server with an SSL Certificate.
How Does Symmetric Encryption Work?
In Symmetric Encryption, only one key used for both encryption and decryption of a message that is being shared through a communication channel. Also known as the conventional encryption method, Symmetric encryption happens to be the oldest known method of encryption with the Caesar cipher falling in this category.
In this method, the plain text gets encrypted and then converted to the cipher text using an encryption algorithm and a key. On reaching the intended receiver, the ciphertext gets converted back to plain text utilizing the same key that was applied for encryption, and a decryption algorithm. The key used can be as easy as a secret number or just a string of letters.
We can use a shift cipher, which is a simple Symmetric Encryption technique, to demonstrate this. If your plain-text is, “COME TOMORROW” and your secret key is to shift each letter by three positions, then for instance letter “C” in the text becomes the letter “F” in the cipher-text. This is precisely what is referred to as the Caesar cipher. Your plain text above will, therefore, look like “FRPH VRPRUURZ” after encryption. At first glance, the cipher message will be incomprehensible to any eavesdropper. However, once it is decoded using the secret key, it reverts to plain text once more.
Examples of modern Symmetric key encryption algorithms include block ciphers such as Blowfish, AES, DES, Camellia, and Serpent, or stream ciphers such as FISH, RC4, QUAD, Py, and SNOW.
What is Asymmetric Encryption?
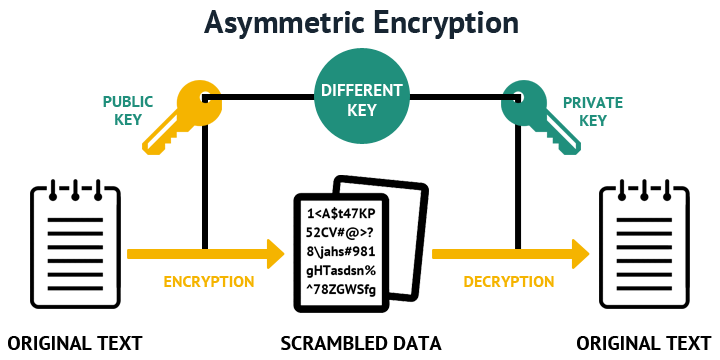
Asymmetric Encryption also called as Public Key Cryptography and it uses two different keys – a public key used for encryption and a private key used for decryption, that is used in SSL handshake process.
Encryption is applied to some extent in almost all communication networks. Though it used to be limited to government communications and military installations, the advent of the widely used Internet made the urgency of securing information channels a priority, hence making encryption the mainstream solution.
How Does Asymmetric Encryption Work?
This is an encryption technique that utilizes a pair of keys (a public key and a private key) for the encryption and decryption processes.
The public key is normally used for encryption while the private key is applied for decryption of the message.
Whereas the public key can be made freely available to any person, who might be interested in sending a message, the private key remains a secret well kept by the receiver of the message.
A message encrypted using a public key and an algorithm will be decrypted using the same algorithm plus a matching private key that corresponds to the public key used.
The use of two keys in Asymmetric encryption came into the scene to fix an inherent weakness with the symmetric cipher. If an eavesdropper gets hold of the secret key in Symmetric encryption, then the whole point of encryption becomes useless.
The probability of this happening is quite high since the secret key might have to be sent through unsecured channels of communication.
Asymmetric encryption offers a security solution by applying two keys, whereby one is public and the other one is Private key.
Asymmetric key-pairs used in SSL Handshake (as a sort of verification method) – In this Handshake process, SSL/TLS connection is established between Server and Client’s browser before the beginning of data transmission.
If a message is encrypted with a public key, then it can only be decrypted using a private key and vice versa. As a matter of fact, Asymmetric encryption is commonly used in our daily communication channels, particularly over the internet. Some of the modern Asymmetric key encryption algorithms include RSA, WELGamal, PGP, Elliptic curve techniques, SSH, and many others.
Conclusion
As a faster technique, Symmetric encryption is mostly used for bulk data transmission. On the other hand, the Asymmetric encryption being a complex and slower encryption technique comes in handy for exchanging keys.
Therefore, the kind of encryption algorithm to be used in any given circumstance depends on the task at hand.
With the rampant cases of hacking communication systems, encryption experts must always ensure that they stay a step ahead of the hackers. For instance, the Asymmetric key cryptosystems’ security depends on a small set of number theory problems that are deemed difficult to decipher, though they were never mathematically proven as so.
This means that any advances made in the number theory might one day make factoring a very easy problem hence compromising the security of the Asymmetric key cryptosystems.




Comments
Post a Comment