OpenSea $1,700,000 Phishing Hack Analysis
OpenSea, the world's largest and most used NFT exchange, suffered a major attack on 2/19/2022, which cost users over 640 ETH worth of NFTs. Additionally, Etherscan may have suffered a coordinated DDoS attack in wake of this exploit in an attempt to block users from revoking access to their NFTs.
In this write-up, I'll take a look at the smart contract (Decompiled) used in this attack, and break down the inner workings of what it's doing at each step. I aim to figure out how this attack happened, as well as how it can be prevented in the future.
Technical Breakdown
The transaction I am going to break down can be found on Etherscan. In order to get a better look at what's happening behind the scenes, I'll also use ethtx.info.
The transaction begins with the attacker interacting with his contract with some calldata, which appears to be a signature for a token sale. At this time, I believe that this signature was somehow phished and stored from the victims in this attack.
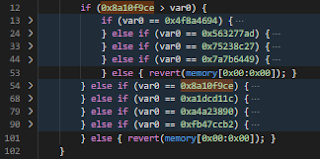
When taking a look at the decompiled bytecode, this assumption of a phishing attack is strengthened, as it appears to be a targeted attack with a switch case for each victim built into the smart contract.
Each switch case seems to be based on msg.data that is sent to the contract, which returns a different fallback function for each case. This fallback function builds a staticcall to WyvernExchange.atomicMatch_ method, which essentially begins the transfer process from the victim, janclarin.eth, to the attacker, all for a cost of 0 ETH.
Since the attacker's contract is calling this function, providing the calldata for both calldataBuy, calldataSell, which came directly from msg.data, we can conclude that this was indeed a targeted phishing attack.
The events emitted by this transaction tell the same story: The attacker was able to call WyvernExchange.atomicMatch_ on behalf of the victims, transferring NFTs to himself for a grand total of 0 ETH.
Future Prevention
Phishing attacks will be around forever as long as there are people who fall for it. In order to stop these attacks, people need to know more about how these attacks work, how to spot them, and how to report them.
Here's the most correct recap of what's happening with OpenSea right now.
— Dan Guido (@dguido) February 20, 2022
tl;dr The security of web3 platforms depend entirely on wallets with universally poor security UX, and there's very little the platforms can do about it. https://t.co/065hiXtQ53
Protecting Users Against Phishing
A wide range of technical approaches are available to prevent phishing attacks reaching users or to prevent them from successfully capturing sensitive information.
Filtering out phishing mail
Specialized spam filters can reduce the number of phishing emails that reach their addressees' inboxes. These filters use a number of techniques including machine learning and natural language processing approaches to classify phishing emails, and reject email with forged addresses. Popular mail service from Google and Microsoft have these features are built-in and just need to be enabled. The best practice is to automatically turn on and apply future recommended settings. This ensures maximum protection for email and attachments for your email box.
- Attachments—Protection against suspicious attachments and scripts from untrusted senders. Includes protection against attachments types that are uncommon for your domain—these can be used to spread malware.
- Links and external images—Identify links behind short URLs, scan linked images for malicious content, and display a warning when you click links to untrusted domains.
- Spoofing and authentication—Protection against spoofing a domain name, employee names, email pretending to be from your domain, and unauthenticated email from any domain. Unauthenticated emails display a question mark next to the sender’s name. Spoofing protection can be turned on for private groups, or for all groups.
Browsers alerting users to fraudulent websites
Another popular approach to fighting phishing is to maintain a list of known phishing sites and to check websites against the list. One such service is the Safe Browsing service. Web browsers such as Google Chrome, Mozilla Firefox and Safari all contain this type of anti-phishing measure.
An approach introduced in mid-2006 involves switching to a special DNS service that filters out known phishing domains: this will work with any browser, and is similar in principle to using a hosts file to block web adverts. In 2016 Google has opened its Public DNS free service with enhanced security features. When you use Google Public DNS, you are changing your DNS "switchboard" operator from your ISP to Google Public DNS.
In most cases, the Dynamic Host Configuration Protocol (DHCP) automatically configures your system to use the IP addresses of your ISP's domain name servers. To use Google Public DNS, you need to explicitly change the DNS settings in your operating system or device to use the Google Public DNS IP addresses. The procedure for changing your DNS settings varies according to operating system and version (Windows, Mac, Linux, or Chrome OS) or the device (computer, phone, or router).
Augmenting password logins
The Bank of America website is one of several that asks users to select a personal image and displays this user-selected image with any forms that request a password. Users of the bank's online services are instructed to enter a password only when they see the image they selected. However, several studies suggest that few users refrain from entering their passwords when images are absent. In addition, this feature (like other forms of two-factor authentication) is susceptible to other attacks.
A similar system, in which an automatically generated "Identity Cue" consisting of a colored word within a colored box is displayed to each website user, is in use at other financial institutions. Security skins are a related technique that involves overlaying a user-selected image onto the login form as a visual cue that the form is legitimate. Unlike the website-based image schemes, however, the image itself is shared only between the user and the browser, and not between the user and the website. The scheme also relies on a mutual authentication protocol, which makes it less vulnerable to attacks that affect user-only authentication schemes. Still another technique relies on a dynamic grid of images that is different for each login attempt. The user must identify the pictures that fit their pre-chosen categories (such as dogs, cars and flowers). Only after they have correctly identified the pictures that fit their categories are they allowed to enter their alphanumeric password to complete the login. Unlike the static images used on the Bank of America website, a dynamic image-based authentication method creates a one-time passcode for the login, requires active participation from the user, and is very difficult for a phishing website to correctly replicate because it would need to display a different grid of randomly generated images that includes the user's secret categories.
Transaction verification and signing and Two Factor Authentication
Solutions have also emerged using the mobile phone (smartphone) as a second channel for verification and authorization of banking transactions. Apps like Authy provide a unified facade for all Two Factor Authentication supporting sites.
Limitations of technical responses
An article in Forbes in August 2014 argues that the reason phishing problems persist even after a decade of anti-phishing technologies being sold is that phishing is "a technological medium to exploit human weaknesses" and that technology cannot fully compensate for human weaknesses. As security researcher Dan Guido tweeted shortly after the OpenSea attack:
Spotting Phishing Scams
In order to spot phishing scams and keep yourself safe, heres a few tips you should follow when reading emails:
- Always check that the sender comes from the real domain.
- If an address contains typos, or a domain that's not associated with the real entity, its fake. For example: security@opensea.ml , security@opensea.co, noreply@metamask.com aren't associated with the real domain, opensea.io or metamask.io.
- Check if the email was sent securely. Nowadays, this is less important since most spoofed emails are automatically sent to spam. However, it's always good practice to check to see if an email was sent securely, because anyone with an IMAP server can spoof an email address. In order to check if an email was spoofed, just make sure it has a valid certificate attached. Don't click links without checking them first. In all modern browsers, hovering over a link will give you the ability to check where you're being taken. If this domain isn't familiar to you, don't click the link. If something is urgent, go log-in to your account and check there.






Comments
Post a Comment