Proof of Work (PoW)
Proof of Work (PoW) is a central part of cryptocurrency and blockchain technology. But what is Proof of Work (PoW) and why is it so important to cryptocurrency? Here’s everything you need to know about the protocol that gave us Bitcoin (BTC).
What Is Proof of Work?
Proof of Work (PoW) is a protocol designed to make digital transactions secure without having to rely on a third party. Essentially, PoW requires members of a community to solve challenging puzzles. This work builds on previous puzzle solutions. As a result, PoW is a way of verifying current and past transactions. Additionally, the work that goes into solving the puzzle generates rewards for whoever solves it. In the world of cryptocurrency, that’s basically what “mining” is. Proof of Work (PoW) is a foundational concept for anything having to do with blockchain.
Background
The concept behind Proof of Work (PoW) was originally invented by Cynthia Dwork and Moni Naor. More specifically, they explained the idea in a paper published in 1993 called “Pricing via Processing or Combatting Junk Mail.”
A few years later, in 1999, Markus Jakobsson and Ari Juels expanded on the original idea. That year, they published a paper called “Proofs of Work and Bread Pudding Protocols.” This paper is where the term Proof of Work (PoW) was coined.
Now, fast forward to 2008. That year, Satoshi Nakamoto published the Bitcoin whitepaper, “Bitcoin: A Peer-to-Peer Electronic Cash System.” Here, Nakamoto explained, What is Bitcoin? He also put forth a method for applying Proof of Work (PoW) to cryptocurrency.
From that point on, PoW has become a key element of cryptocurrency and blockchain technology.
How PoW Works
Proof of Work (PoW) is a piece of data that is hard and costly to produce, but easy to verify once it’s been generated.
Many times, people explain this data as the solution to a puzzle. Essentially, members of a given community work to solve a complex puzzle. This is the “work” in Proof of Work (PoW).
In order to create the data—or solve the puzzle—a miner must compute through a very complex equation. Because each attempt at the equation builds on previous solutions, any new solution essentially verifies previous work.
At the same time, the work required to solve the equation generates a new piece of data. This is then added to the growing chain of data. From there, the process basically starts over again.
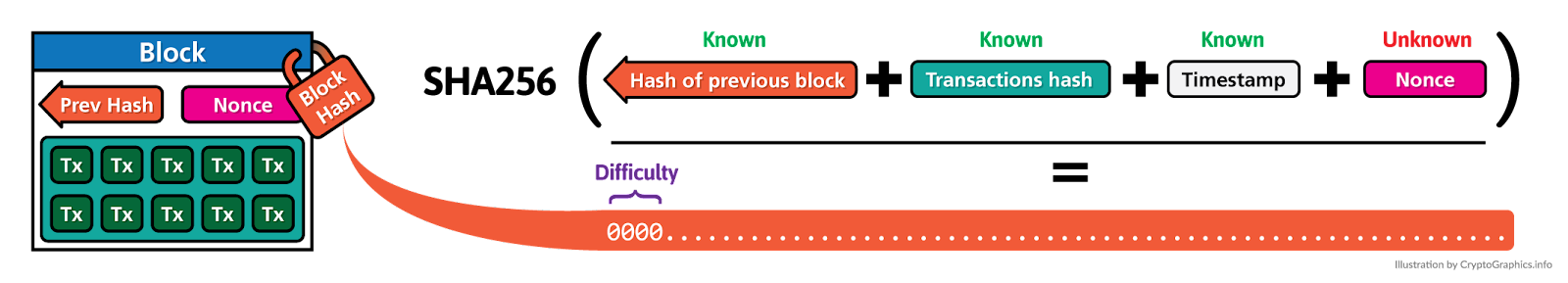
Proof-of-Work operates on the principle that it is expensive to add a block of new transactions to the blockchain. The cost of a block is the work that has to be done: calculation (better known as mining). A node has to calculate the correct hash (signature) for the block in order to secure the block and place it on the blockchain, in turn freeing another (new) block. A correct hash is a hash that fits the (pre-determined) difficulty pattern. In Bitcoin’s case this is a number of leading zeroes.
Advantages
There a number of key advantages to using Proof of Work (PoW).
Because it’s very hard to do the work, PoW reduces the risk of a 51% attack, of which we'll explain more in the next article. At the same time, each solution is easy for the community to verify. This makes it easy to check all transactions for trustworthiness. It doesn’t rely on a single third party transactor. This builds a “trustless” and transparent network. PoW also sets a limit on how many new blocks of data can be generated. For example, miners can only create a Bitcoin (BTC) block every 10 minutes.
Disadvantages
PoW is expensive, labor-intense and uses a lot of energy. Creating a new block requires a lot of energy, which a recent study that compared cryptocurrency mining to aluminum mining emphasized. For example, Bitcoin’s annual carbon footprint is bigger than Switzerland’s. Additionally, PoW tends to be “pointless” work. That is, the work does nothing more than solving the arbitrary puzzle of the algorithm. Many see this as a lot of wasted computing potential. Some see PoW as a more expensive, outdated version of Proof of Stake (PoS), which is another way to maintain the network and we'll cover in the next articles.
Breaking It Down
The transactions interconnect from the bottom up, but the protocol works top to bottom. To be more specific, let’s break the above graph down a bit further:
Terminology
- T stands for the transaction.
- Hash is the answer to the equation you’re trying to solve.
- Merkel Root is a hash of all previous hashes combined
- Nonce is short for “number used once” that you use in verifying blockchain transactions. It is only used once in order to secure the transaction.
- Cryptographic Hash Function is an equation into which the blockchain inputs a transaction and outputs a string of letters and numbers mathematically related to it that represent it.
- Hash with Difficulty Target is the hash for that block. It must be smaller or equal to a figure determined by the blockchain for the miner to receive the reward, as determined by the “difficulty target.”
Steps
If you want to mine and get the reward for completing PoW, you have to process a block of transactions. You begin your PoW on top of an already-completed hash.
- Pick a “nonce,” which is short for “number used once.” At this point, your PoW is starting to take shape. You’ve got: previous hash + current transactions you’re processing + any random nonce.
- You’ll repeat this process until you find the nonce that completes the puzzle. The “final answer” you’re looking for is established by the parameters of any given blockchain. For example, in Bitcoin, the “answer” is always some integer between 0 and 4,294,967,296.
- When you find the right nonce you essentially solve the puzzle and you are rewarded with currency.
- At that point, somebody else will begin mining by building on top of the hash you just completed.
Because there are so many possible combinations, and you have to work through so many nonces to find the right one, it takes tons of computing power.
Once PoW is completed, it’s a block of data and it’s public. It cannot be altered, and if somebody tries to mess with a hash everybody sees it. This is part of where blockchain’s security comes from.
Encouragingly, the crypto community seems to be addressing the waste that’s built into PoW. For example, Ethereum is currently exploring ways to switch to Proof of Stake. This model could cut back on the amount of energy required to maintain the blockchain.



Comments
Post a Comment